Page History
...
- If using Servoy for storing user data, create a user database for the application or set of applications. Be sure to at least include a username and password column in the database.
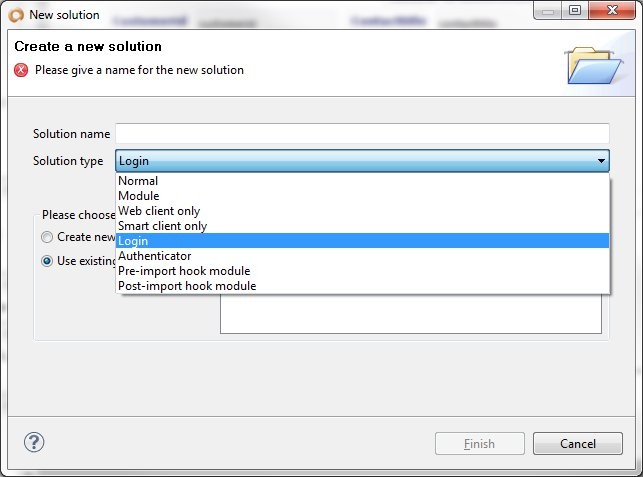
- Create a login solution. A login solution should have the following attributes:
- Solution type of login
- A login form set as the first form.
- The login form should have fields (normally form variables) for entering a username and password
- A button or method that will validate the fields are not null and finally call the authentication method of the authenticator solution. See Login Method Example.
- The login solution has no database access, so if there is any validation done during the login process (find tenant id, verify user exists, etc.), the login solution must call an authenticator solution for any database information.
- Solution type of login
- Create an authenticator solution (during the solution creation process, same as login solution). The authenticator has the following attributes:
- Solution type of authenticator
- Includes a global method to authenticate users. This method will check the users table or call external authentication to authenticate. This method will also log the user into Servoy. See Authenticator Method Example.
- Can also include other methods for checking a user or getting a tenant id.
- The authenticator solution is not a module of the solution, but must be in the repository of the application server or in the developer's workspace.
- Solution type of authenticator
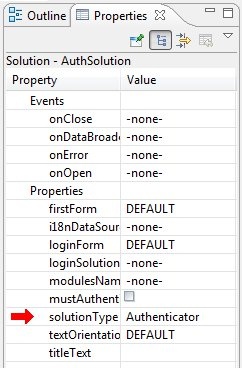
- Set the login solution property to the login solution you have just created.
- Deploy the application, making sure to include the authenticator solution if you do an import on the application server. The custom login form will appear when launching the solution.
| Note | ||
|---|---|---|
| ||
When first introduced in Servoy, this method of using Login and Authenticator solutions was referred to as Enhanced Security. If you are looking for any references to this method, you may try searching Enhanced Security. |
Solution onOpen Method
For almost every implementation of security, the solution should have an onOpen method assigned. This event is triggered right after the authentication process is complete. Some of the functions of this method in regards to security include:
...
The code below is an example of a typical custom login method. In this scenario, the login page contains the following form variables:
- userName - the name entered at login
- password - the password entered at login
- errorMessage - any error messages returned to the login solution.
The tenant is verified during login before actual authentication occurs.
| Code Block |
|---|
function login(){
var tenantID, userID;
errorMessage = null;
if(!userName){
errorMessage = 'Please specify a user name';
return false;
}
if(!password){
errorMessage = 'Please specify a password';
return false;
}
var tenantID = security.authenticate("myAuthenticator","getTenant",[userName]);
if(tenantID){
if(security.authenticate("myAuthenticator","loginUser",[userName,password])){
return true;
} else {
errorMessage = "No tenant found. Please check your password";
}
}
errorMessage = 'Login Failed';
}
|
Example Authentication Method.
The code below is an example of a typical authentication method.
| Code Block |
|---|
function loginUser(user, password) {
if (!(user && password)) {
application.output('Unexpected credentials received', LOGGINGLEVEL.DEBUG);
return false;
}
var authenticated = ... //either query database or use LDAP
if (authenticated) {
var ok = security.login(user, user, ['group']) // Assume a group for each department
application.output('User ' + user + ' authenticated: ' + ok, LOGGINGLEVEL.DEBUG);
return ok;
}
application.output('User ' + user + ' could not be authenticated', LOGGINGLEVEL.DEBUG);
return false;
}
|
Note that you have the choice of querying the database or getting an external authentication. You may also read a user groups table to create the array of groups the user has privledges with. Also not that the only thing that is returned is a true or false and that reporting errors to the user does not occur at the authenticator level.