Page History
Servoy provides the ability to log any data change or data read in a table in Servoy. This data is stored in a table specified in the database and can be reported, displayed, and used within a Servoy solution.
| Stoc |
|---|
Configuring Audit Logging
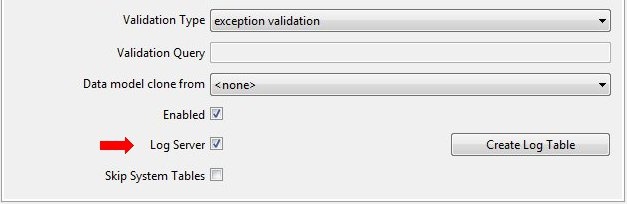
Configuring Servoy for audit logging is done in the database server connection pages. Any database server can contain the log table. To enable a server to be the log server, select Log Server in that database server's configuration editor.
The log table can be a table with all the other data tables for your the solution, or it could be in its own separate database server. Some reasons for having a separate database server for the log table include:
- As the audit log table could be very large, it can be stored separately from the other data tables.
- The log database could be optimized separately for inserting records, as audit logging is primarily inserting records into the log.
- Separate backup or archive strategy for the audit log database.
- Optimal performance - The tracking feature does decrease performance. The speed impact on the solution largely depends on the back-end database the developer is using.
Once the database server has been decided, check the Log Server box and click the Create Log Table button. A table named "'log" ' will be created in the database server. Now audit logging is available for any table in the resource resources project (or on the application server for Servoy Server).
To log any changes to or views for a table, do the following:
- open the table in the table editor
...
- select the
...
- Security tab, and select the desired group
...
- select the Explicit settings and enable the Tracking(Insert/Update/Delete) and/or Tracking(Select) option.
...
If Tracking(Insert/Update/Delete) option is enabled any adds, edits, or deletes to the table will be tracked for the selected group.
If Tracking(Select) is enabled any views of data to the table will be tracked for the selected group.
| Info |
|---|
Tracking views of data is HIPAA Security Rule compliant. |
Using Audit Log Data
As the log table is simply another database table, a developer can builds build forms against the log table to allow users the ability to read and work with the data. Data within the audit log could also be used to access any changed record in the database.
...
- event_time - The time the change occured
- log_id - The auto incrementing ID of the log table
- log_action - The type of change action that occurred. 1=delete; 2=insert (or add); 3=update(changed record); 4=view(data read)
- server_name - Name of the DB server registered in the preferences window
- table_name - Name of the table affected by the changeaction
- column_name - Name of the column (field) in the affected by the changeaction
- pk_data - Primary key data for the record being changed/viewed. Format: x.yyyy; x=number of characters in the key. y=the actual key value. Multiples are separated by semicolons
- old_data - The old data value before the change (will be null for views)
- new_data - The new data value after the change or the data that is read from database
- user_uid - The UID value for the user making the changeaction. This can be set during the login process or is stored in the repository if using basic authentication.